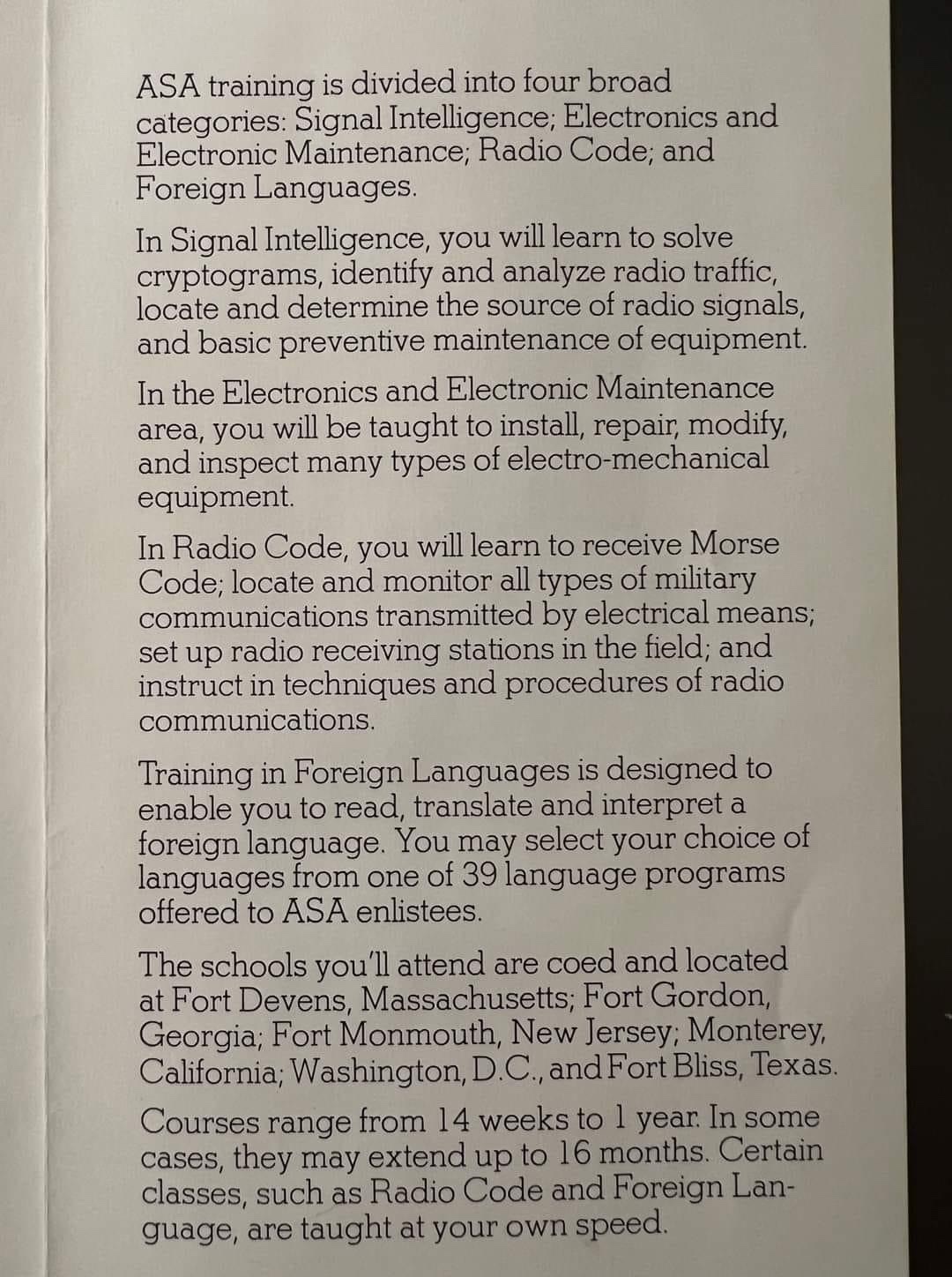
ELLICOTT CITY, Md. — Originally from the San Francisco Bay Area in California, Dr. Tom Glenn originally enlisted in the Army so he could attend the Army Language School — later called the Defense Language Institute, or DLI. With a passion and knack for linguistics, Glenn taught himself French and Italian as a child, studied Latin during high school and German during college.
With a craving for more, Glenn enrolled in DLI with the hopes of learning Chinese.
“I wanted to go to the best language school in the U.S., maybe in the world,” he said. “But when I got [there], they told me they weren’t going to teach me Chinese, they were going to teach me a language I had never heard of: Vietnamese.”
Glenn was a Soldier and had to follow orders, so he spent all of 1959 learning Vietnamese. He spent six hours a day in class with two hours of private study each night for a full year.
“I graduated first in my class of ten,” he said. “I asked the Army to send me to Vietnam but [they said] they had nothing going on there.” Instead, Glenn was assigned to the National Security Agency, or NSA, at Fort Meade, Maryland.
Still hoping to study Chinese, Glenn enrolled in George Washington University in Washington, D.C. as a part time graduate student. Glenn went on to earn a master’s degree in government and a doctorate in public administration.
By the time Glenn finished his enlistment in 1961, he said he was “comfortably speaking” Vietnamese, Chinese and French; the three main languages spoken in Vietnam.
The NSA immediately offered Glenn a job at “five steps above the normal level” and sent him to Vietnam for the first time in 1962 as a civilian.
“Between 1962 and 1975, I spent more time in Vietnam than in the U.S.,” he said.
Despite being a civilian, Glenn lived with the military as if he were still a Soldier.

Tom Glenn poses for a photo in his fatigue uniform in Dak To, Vietnam in 1967. One morning while assisting U.S. 4th infantry division and 173rd airborne brigade, Glenn woke up to find his uniforms missing. Some of the Soldiers at his camp had “snitched” his fatigues and taken them to a local tailor whom they paid to sew tags above the breast pockets that read ‘Glenn’ and ‘Civilian.’ (Photo Credit: Courtesy photo)
“I was one of them — sleeping on the ground next to them, eating [field rations while] sitting in the dirt by their side, using their latrines and going into combat with them,” he said. “I was the only civilian I knew who was willing to put his life on the line by working with the military in combat on the battlefield.”

Tom Glenn in Saigon, Vietnam in 1962 (Photo Credit: Courtesy photo)
Glenn’s job was in intelligence; using signals intelligence, intercepting and exploiting the enemy’s radio communications, informing friendly forces on what enemy force intentions were and where they were.
He says that the strongest human bond he’s ever seen was that between two men fighting side by side.
Glenn spent his thirteen years in Vietnam all over the country, “wherever combat was going on.” He worked most often in central Vietnam, just south of the demilitarized zone that separated North and South Vietnam. The day-to-day was just like any other Soldier in combat.
“[The days were] defined by the boredom of waiting and the terror of close combat,” he said.
Glenn wants Americans to know the “grisly horror” of war. He wants citizens to respect and admire service members who “put their lives on the line for our good.”
After the Vietnam War, Glenn’s readjustment to civilian life would have been more difficult had he been sent straight home. Instead, he was sent abroad to serve on the battlefield all over the world after Saigon fell in 1975.
Glenn retired from NSA in 1992.

Tom Glenn in Saigon, Vietnam in 1974 (Photo Credit: Courtesy photo)

A Civilian Meritorious Medal that Glenn earned for saving lives during the fall of Saigon, Vietnam under fire in 1975 (Photo Credit: Courtesy photo)
“Welcome home, brother”
When Glenn meets other Vietnam veterans, he puts his hands on their shoulders and looks them in the eye. They share an experience unknown to other Americans.
For years following the war, many Americans saw Vietnam as “the war we never should have been involved in.” During those years, Glenn never mentioned his service overseas.
“Then, several years ago, I was invited to a welcome-home party for Vietnam veterans,” he said. “After some hesitation, I went. A bunch of young people, who hadn’t even been born before the end of [the war], shook my hand, hugged me and thanked me for my service.”
Glenn urges other Americans to approach those who served and thank them. Only then will that service member know that their service is “worthy of gratitude.”

Award-winning author
“The real adjustment [came] thirty years ago when I retired as early as I could [to] write full time,” Glenn said. “I was so intent on writing that the transition was a relief rather than an adjustment.”
Glenn’s first book is titled “Friendly Casualties” and consists of a collection of short stories to highlight the horrors of war. He chose to write about Vietnam because of his post-traumatic stress injuries, or PTSI. “[It] wounded my soul,” he said.
He learned that the only way to survive his injuries was to face the memories “head-on.” The best way to force himself to face those memories was to write it all down, which has resulted in six books and 17 short stories as of March 2022.
Glenn’s books are categorized as “fact-based fiction” which he said is the only way he could “delve into the emotions [he] lived through in real life.” He said he’s lived through experiences “far more compelling” than anything completely made up.
“I want people to know what [it was like],” he said. “I needed to vent, to stand face-to-face with my memories and learn to live with them.”
By Megan Clark