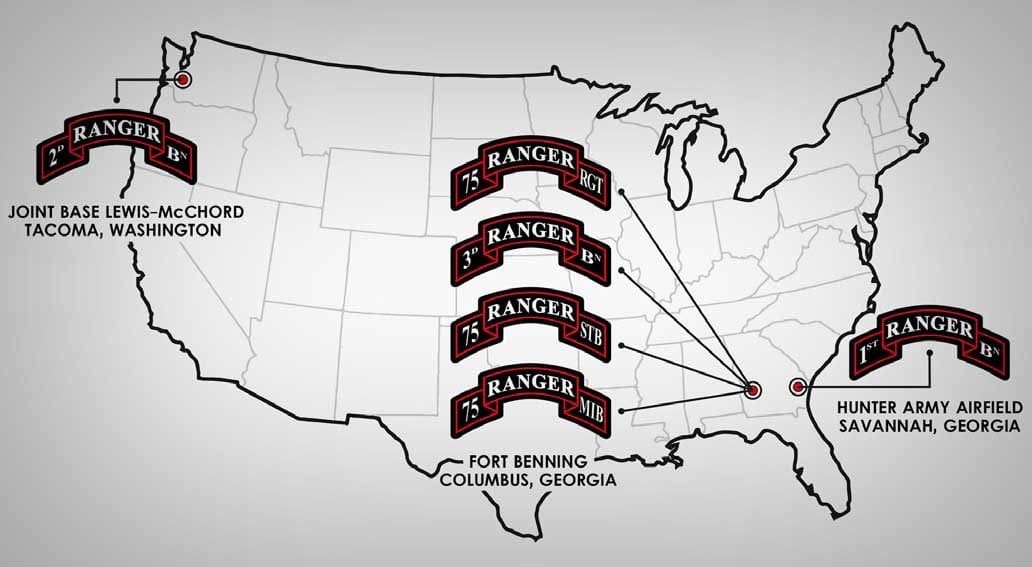
In addition to Military Intelligence in each of the Ranger Battalions and Regimental headquarters, the 75th has a dedicated Military Intelligence Battalion at Fort Benning.

In addition to Military Intelligence in each of the Ranger Battalions and Regimental headquarters, the 75th has a dedicated Military Intelligence Battalion at Fort Benning.
The company has also secured follow-on orders worth $8 million to supply its C-IED system, the C-Guard RJ, in both portable & vehicular configurations, to a state police force in Asia.

November 11, 2019 – Netline Communications Technologies Ltd. – a leading developer and manufacturer of high-end electronic warfare and spectrum dominance solutions – is strengthening its presence in the APAC region, with several new contracts recently signed in this market.
One significant contract is a program to provide the C-Guard Reactive Jamming (RJ) Vehicular System, a vehicle-installed system that provides counter-IED (improvised explosive device) protection, to head-of-state motorcades in a Southeast Asian country. This unique solution both detects the threat and provides an immediate response, preventing remote detonation of radio controlled IEDs by transmitting jamming signals around the entire convoy. The system will be delivered by the end of the year.
Other contracts signed by Netline include follow-on orders for the supply of both vehicular and ManPack (MP) C-IED systems, to a state police force in Asia. In its MP configuration, C-Guard RJ is carried by frontline forces in a single backpack unit, preventing attempts to activate IEDs around tactical forces when on the move.

IEDs, such as roadside bombs, are activated by radio-controlled devices (cell phones, walkie talkie, etc.), and have become a common threat in today’s asymmetric warfare, as they are easy to make. Delivering benefits that include superior reactive jamming capabilities, wide coverage, simple operation by ground forces within a specific radius, and compliance with a wide range of Mil-STDs and radiation safety regulations, Netline’s C-Guard family of reactive jamming systems provide a real-time counter-IED solution.
“We are pleased to further establish our presence in Asia, both with new contracts and business, and by securing follow-on orders from existing customers,” says Yallon Bahat, CEO of Netline. “Both our new and repeat orders are an indication of our customers’ satisfaction with Netline’s technology and products. We appreciate the cooperation with the different security agencies in these countries and believe this cooperation will be extended to additional future projects, enabling our customer to align their EW security strategy with the rapidly evolving threats, by using Netline’s high-end, advanced EW technology.”
JOINT BASE LANGLEY-EUSTIS, Va. (AFNS) —
Gen. Mike Holmes, Air Combat Command commander, discussed the designation of the 16th Air Force as a new information warfare numbered air force Sept. 18 at the Air Force Association’s Air, Space & Cyber Conference in National Harbor.

ACC will integrate 24th Air Force and 25th Air Force capabilities into a new organization under a single commander who will be responsible for providing information warfare capabilities to combatant commanders with the speed to match today’s technological environment.
“By having cyber and all the intelligence, surveillance and reconnaissance tools together, one of the things it allows me to do is build a collection plan in advance before I do something and am able to have better information to support better decisions for our warfighters,” he said. “The Air Force is not going to run independent information warfare campaigns, but we’ll build those, organize, train and equip tools for combatant commanders.”
The heritage of 16th Air Force pays tribute to a group of highly decorated Airmen with a history of continued excellence in joint warfighting, strategic deterrence and military partnerships. During the Balkans air campaigns in the 1990s, the 16th Air Force pioneered efforts in the way the Air Force conducts intelligence operations, setting the foundation for operating in a continuously evolving information environment.
“We want to arm our leaders with options they can use that are proportional to the things that peer adversaries are doing,” he said. “We think we can present more robust teams with better intelligence support behind them and present some information ops options, which we have some game at already, but to improve that and be able to offer it on a larger scale to more combatant commanders at once.”
Activating 16th Air Force emphasizes the organization’s continued excellence in addition to its early use of integrated information systems and emerging technologies, such as remotely piloted aircraft. Just as the 16th Air Force made history bedding down the RQ-1 Predator at Taszar, Hungary, to provide enhanced ISR capabilities in the Balkans, it will soon make history again in the expanding arena of information warfare.
“The activation of 16th (Air Force) will synchronize the mission areas of ISR, electronic warfare, cyber and information operations capabilities,” said Holmes. “This integrated capability will provide multi-domain options to component and combatant commanders around the globe.”
The 16th Air Force will be located at Joint Base San Antonio-Lackland, Texas, where ACC will hold an activation ceremony later this year.
By Staff Reports, Air Combat Command Public Affairs
WASHINGTON — The military is doing a great job recruiting cyber talent into military and civilian service, but retention is more difficult, said the deputy assistant secretary of defense for cyber policy said at the Billington Cybersecurity Summit in Washington.

“We have people lined up out the door that are ready to come onboard and do the mission, whether it’s cyber operations or traditional cybersecurity,” Burke E. “Ed” Wilson said at last week’s event.
Wilson said Congress gave the military some unique authorities that have helped in hiring qualified civilians.

“This has allowed us to hire with more agility based on the talent,” he said. “That’s been a big win, and we’ve seen very good results over the last 18 months.”
But the challenge is retention. “Clearly, we don’t do well on salary in the military, but we’ve been able to handle that with bonuses,” Wilson said, adding that the strategy is working well, except in some niche areas.

John “Jack” Wilmer, the Defense Department’s deputy chief information officer for cybersecurity and chief information security officer, said young people are attracted to the military because it has a “cool mission.” To keep them, the military provides them with some really great training opportunities, he said.
Cyber games, for example, allow them to go toe-to-toe with some of the best cyber warriors from other countries, he said. “We try to incentivize people and connect them with opportunities,” he added.
Army Lt. Gen. Stephen Fogarty, commander of Army Cyber Command, said another way to incentivize the workforce while solving difficult cyber problems is to organize the cyber workforce into teams.
Teams can be made up of people who are experts at electronic warfare, information operations, intelligence, developers, malware analysts and other specialties based on the type of operation they’re engaged in, he said.
The teams can extend outside the U.S. military and include foreign military partners, commercial vendors and academia, Fogarty said.
“We very rarely act without a consortium of partners. I can’t think of a single operation that didn’t include multiple partners,” he said. “Young people reach out to their peers and build their own networks. They’re very successful at building these ad hoc relationships, and they get after the mission.”
By David Vergun, Defense.gov
Rohde & Schwarz demonstrates tactical and strategic intelligence and digital communications sovereignty, as a systems partner and integrator for planning, developing, manufacturing and implementing secure communications architectures and monitoring networks. The privately owned company showcases an innovative portfolio of interoperable, high-performance solutions for deployment on land, in the air and at sea.
London, September 9, 2019 – At this year’s DSEi, taking place in London, Great Britain from 10 to 13 September 2019, Rohde & Schwarz pushes information superiority, situational awareness and spectrum dominance to the next level, presenting its full technology portfolio on booth S1-350. Showcased are EW/SIGINT (electronic warfare/signals intelligence) systems, integrated communications on the high seas, on land and in the air, networked encryption devices and test and measurement solutions for radar and EW, alongside counter-UAS systems.

Rohde & Schwarz will showcase its operationally proven NAVICS integrated communications system for internal and SOVERON for external communications on all classes of ships. Relying on commercial IT technology to a large extent, the system is especially cost-effective, and its modern graphical user interface (GUI) makes it intuitive to operate. The system is fully IP based, allowing the integration of further communications services such as Voice-over-IP (VoIP), broadcast, alarm functions and shipborne telephone systems. Rohde & Schwarz will equip the Royal Navy’s Type 26 Global Combat Ship with an integrated communications system, built around the NAVICS, under a contract from BAE Systems, covering both internal and external communications.
As a leading supplier of EW/SIGINT solutions, Rohde & Schwarz is THE One-Stop Shop for reliable and field-proven EW, offering an exceptional portfolio and comprehensive functionality. In London, the company will showcase advanced EW systems for enhancing the situational awareness during operations in the field. The presented ELINT system features components of next generation ELINT intercept solutions that have been established on the market for years. The core component is a new 8-channel wideband ELINT concept, with 2GHz bandwidth, collecting and analyzing modern LPI signals and likewise legacy radar emissions. Exhibits also include a cellular network analysis system for supporting reconnaissance missions with focus on non-military communications. Moreover, Rohde & Schwarz will present a counter-UAS solution that provides reliable drone detection and countering capabilities even under challenging signal scenarios. The modular and scalable systems can be deployed on a variety of platforms and are in operation in the field several dozen times.
With its expertise in test and measurement, Rohde & Schwarz is also a leading provider of dedicated test solutions that help developers and engineers address the latest challenges in advanced radar and EW system design. At DSEI, the company will showcase its state of the art solutions for testing multifunctional radar systems, radar warning receivers and deceptive jammers/DRFM.
Addressing land-based platform requirements, SOVERON provides government customers with a secure, high-performance network architecture based on state-of-the-art hardware and software. SOVERON creates technological independence, scalable and modular according to customer requirements thus enabling digital sovereignty. As key components of the SOVERON architecture, Rohde & Schwarz presents its innovative SOVERON software defined radios (SDR) for tactical and airborne communications scenarios. For these SDRs, the company has designed high data rate, anti-jam waveforms to match diverse mission requirements. For every communications scenario, users can select the waveform and encryption that best suit their requirements in terms of range, data rate and jam resistance.
Furthermore, Rohde & Schwarz displays a broad range of hardware and software products to effectively protect networks and critical infrastructures against attacks. These encryption solutions protect authorities, organizations and enterprises against espionage and data manipulation. The Rohde & Schwarz network encryption devices are approved by the German Federal Office for Information Security (BSI) and can be used flexibly with many stationary and mobile applications.
ABERDEEN PROVING GROUND, Md. — The Army is advancing its ground-based precision navigation and timing, or PNT, technology to counter spoofing threats and improve operations in a multi-domain environment.
While GPS continues to be the “gold standard” for PNT capabilities, it can be disrupted from a number of frequency interferences such as weather, and man-made or natural terrain, said Col. Nick Kioutas, the PNT project manager.
Near-peer competitors have also demonstrated an ability to “spoof” current GPS technologies. Spoofing can generate position and timing inaccuracies on a battlefield, he said Friday at a media event hosted by Program Executive Office Intelligence, Electronic Warfare and Sensors, or PEO IEW&S.
The Army has taken a layered approach to ensure accurate position and timing data, he said. This approach includes the integration of non-radio frequency technologies on the battlefield, such as inertial-based navigation systems, chip-embedded atomic clocks, and Soldier-worn or vehicle-mounted odometers.
For example, industry officials are currently developing and testing a boot-sensor prototype that tracks a Soldier’s rate of movement, he said.
“It is like a pedometer,” Kioutas said. “If you knew you were walking at a certain pace and all of a sudden your system jumped a kilometer — you know you’re being spoofed.”
The Army also looks to secure access to alternative sources of PNT data through other GPS networks. Program officials have also considered the use of anti-jam antennas on vehicles to ensure access to GPS and PNT signals, Kioutas said.
“Our systems will integrate all these data sources to determine which one we can trust the most,” he said. “If our GPS is spoofed, we can look at our inertial navigation system [or other layered systems], and compare it to one of these alternative signals” to get accurate PNT data.
ELECTRONIC WARFARE

Along with improved PNT capabilities, PEO IEW&S is currently developing an Electronic Warfare Planning and Management Tool, or EWPMT, to manage and control electronic warfare assets in support of unified land operations.
Through the EWPMT, the Army can now visually synergize its EW attack, targeting, and surveillance capabilities to enable the maneuverability of forces. The tool also improves spectrum management operations and assists with the intelligence-gathering process.
Operators can streamline the process between the EWPMT and fires support, in addition to being able to configure their system to generate automated responses to a variety of signals or alerts, officials said.
Once a EWPMT system is triggered, the program will initiate its automated workflow, often distributing information throughout a tactical operations center. Depending on the engagement, operators can initiate a fire mission and provide tactical graphics for support.
“Operational units can now visualize the electromagnetic spectrum,” said Lt. Col. Jason Marshall, product manager for Electronic Warfare Integration.
“EWPMT is the commander’s primary tool to integrate multi-domain operations into their military decision-making process,” he added.
While still under development — EWPMT increment one, capability drop three — is leveraging user feedback to allow EWPMT to support the electronic warfare officer’s techniques, tactics, and procedures, Marshall said. A pool of electronic warfare Soldiers and electromagnetic spectrum managers, or 25Es, from across the Army are involved in the program.
Instead of waiting for EW to become an official part of the targeting process, program officials are trying to get ahead of the curve to fulfill a future requirement, said Capt. Daniel J. Nicolosi, EWPMT assistant product manager.
Currently, EW operators “have nothing,” added Chief Warrant Officer 2 Will Flanagan, senior electronic warfare targeting officer, who is assigned to the operations group at the National Training Center at Fort Irwin, California.
As an operator, Flanagan is highly involved in the EWPMT’s ongoing developmental process.
“With the EWPMT in front of me, I can show the commander where we’re at, and what we can do,” he said. “This will give us that spot on the TOC floor. This is the first tool to allow us to do our jobs.”
Future iterations of the EWPMT program, officials said, will focus on pacing the threat’s capabilities within a disconnected, intermittent, and latent environment. In turn, the program will help refine the Army’s ability to conduct cyberspace electromagnetic activities in support of multi-domain operations and enable the Army to fight and win on a complex battlefield.
VMAX

For the EWPMT to be effective, it relies on fielded communications sensors and other EW transmission devices.
The Versatile Radio Observation and Direction, or VROD, Modular Adaptive Transmission system, known as VMAX, have already been fielded to meet mission requirements.
“VMAX is a lightweight man-portable electronics support and offensive electronic attack system. It is used to find, monitor, locate, and jam RF emitters in real time during tactical operations,” said Ken Gilliard, team lead of the Rapid System Applications Team, which falls under the Command, Control, Communications, Computers, Cyber, Intelligence, Surveillance, and Reconnaissance Center, or C5ISR.
“Its purpose is to create that advantage in the electromagnetic spectrum to provide Soldiers a window to maneuver on the battlefield,” he added.
When VMAX is operating in a support capability, operators can monitor the electromagnetic environment and determine what frequencies an adversary is operating on. Further, Soldiers can use multiple VMAX systems to geo-locate a signal, he said.
Similarly, if VMAX is supporting offensive EW capabilities, it can be used to jam or interfere with the signal within specific frequencies.
VMAX is a self-contained, battery-powered device, which weighs approximately 25-30 pounds, Gilliard said. Soldiers can tether VMAX to a vehicle, a building, or some air platforms. The device can be remotely operated and configured with a wide range of antennas to fulfill mission requirements.
The Army currently owns more than 200 VMAX nodes and 100 VROD nodes, he added. Majority of these devices are already deployed around the globe, many of them supporting operations in Europe and the Middle East.
Story by Devon L. Suits, Army News Service
Illustration by Justin Rakowski
Photo by 1st Lt. Jordan Linder
The company has also been awarded a €65 million contract to supply its Vehicular C-Guard System to the Spanish MOD

August 5, 2019. Netline Communications Technologies Ltd. – a leading developer and manufacturer of high-end electronic warfare and spectrum dominance systems for defense forces and homeland security agencies – is supplying its C-Guard Reactive Jamming (RJ) Manpack system to the IDF. The system is already being operated by the IDF, and is also in ongoing use by ground forces in NATO countries, Asia and Africa.
Improvised Explosive Devices (IEDs), such as roadside bombs activated by radio-controlled devices (namely cell phones), have become a common threat in today’s asymmetric warfare, as they are easy to make. Netline’s reactive jamming system provides frontline forces with a real-time counter-IED solution.
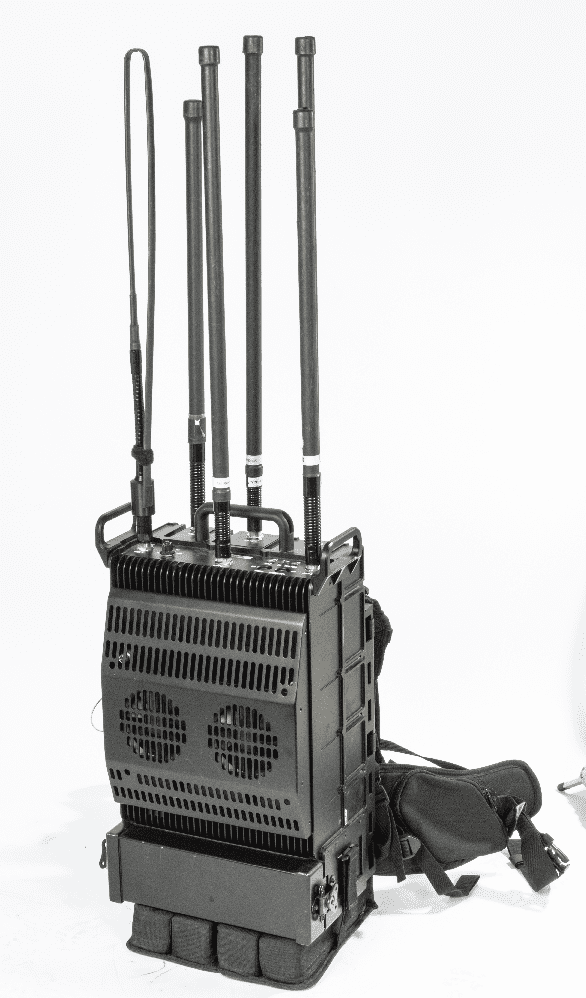
Easily carried into the battlefield, the C-Guard RJ Manpack system detects and prevents IED activation attempts. The system creates a secured zone around the soldiers on the frontline, reacting to real-time situational electronic warfare (EW) threats by both detecting the threat and providing an immediate response of jamming RF signals that are attempting to detonate the IED. The solution’s advantages include superior reactive jamming capabilities, wide coverage, simple operation by an individual soldier to provide protection of personnel within a specific radius, and better overall control of the operational situation, all without requiring any additional hardware.
Netline has also recently secured a €65 million contract with the Spanish Ministry of Defense. In a show of confidence similar to the IDF’s, both in Netline and its advanced jamming capabilities, this is a major contract to supply the C-Guard RJ vehicle system for use in all military corps of the Spanish Armed Forces, due to begin in December 2019.
“We are proud that the IDF and the Spanish MOD have chosen our life-saving systems to protect their forces in a variety of operational missions,” says Yallon Bahat, CEO of Netline. “For us, this is further evidence that our strategic decision to invest in the development of high-end EW technologies is bearing fruit. We have succeeded in bringing the message of EW defensive measures to the ground tactical arena, and will continue to invest in advanced generations to provide solutions for future threats in this field.”