
Army Cyber has posted the DoD Identity Awareness and Protection Management Guide for easy downloading. This guide is intended to be shared widely with work, family and friends. A great resource for families and military units alike!

Army Cyber has posted the DoD Identity Awareness and Protection Management Guide for easy downloading. This guide is intended to be shared widely with work, family and friends. A great resource for families and military units alike!

MOJAVE DESERT, Calif. — In the desert of the National Training Center, Soldiers got an opportunity to try something completely new. Along with the challenges of 14 grueling days of force-on-force and live-fire training exercises, the 3rd Brigade Combat Team, 1st Cavalry Division (3/1 CD) tried out a cyber-based prototype that complements electronic warfare systems to combat enemy drones, which are a growing threat to U.S. ground troops.
Using the Army’s enhanced cyber-enabled Counter-Unmanned Aerial System (C-UAS) capability, Soldiers with the 3/1 CD were able to detect and counter common small drones during their training. The new prototype alerted Soldiers to the presence of a drone and provided a means to target it, for protection across the brigade.
This integration of cyber-enabled prototypes with existing signal, intelligence and electronic warfare capabilities allowed the Soldiers to fix on a target and engage their fires cell, said Capt. Christopher Packard, electronic warfare and cyber electromagnetic activities chief for the 3/1 CD.
“That’s the goal right there, to reach the commander’s end state and to meet his intent for lethal targeting–those are some of the main concepts to focus on,” Packard said. “I think we’ve done well here, getting intelligence information as it’s passed …. that we can use for targeting. I’m looking forward to seeing where this goes in the future.”
CYBER SOLUTION SOUGHT
While the Army has a wide variety of solutions to counter drones, the new capability focused on bringing precision cyber techniques to bear as a complement to those other C-UAS systems. A small group of software developers within the U.S. Army Cyber Command (ARCYBER) and the Defense Digital Service custom-built software, developed a user-focused design and modified commercial off-the-shelf equipment to create pilot systems in early 2018.
Growing demand for a more robust and scalable solution generated a need for a rapid prototype. The Defense Digital Service completed the specialized software of the pilot system and transitioned development of a prototype to the Army Rapid Capabilities and Critical Technologies Office (RCCTO), which crafted an acquisition approach that integrated software and hardware. Working with Tobyhanna Army Depot and ARCYBER, RCCTO launched prototype production in November.
In less than three months, the integrated team sprinted and surged to deliver the new cyber C-UAS capability to the 3/1 CD. The new system is an interim solution that will continue to evolve as the Army applies direct Soldier feedback to improving design and performance. The integrated team is incorporating feedback from the unit’s rotation at the National Training Center (NTC) at Fort Irwin, California, which took place Jan. 7-25, as they develop a phase two prototype, to be delivered later this summer.
“This effort allowed the 3/1 CD to receive valuable C-UAS training ahead of their upcoming mission set,” said Jack Dillon, RCCTO’s cyber lead. “It also provided critical feedback that we are already feeding into the next version.”
A FAST-MOVING TEAM
Receiving a request to produce a never-used-before, cyber-enabled C-UAS on Aug. 22 and delivering it by Nov. 12 is not business as usual. However, ARCYBER, RCCTO and Tobyhanna, working in lockstep, were able to deliver.
“The RCCTO and Tobyhanna helped out with taking it from an advanced prototype and turning it into an engineering design model,” said 1st Lt. Aneesh Patel, with ARCYBER’s Cyber Solutions Development Detachment — Georgia, 782nd Military Intelligence Battalion, 780th Military Intelligence Brigade. “We designed our own hardware and schematics, but what we didn’t have was the proper ability to scale, and I think that’s important in a bridging strategy and for any prototype.”
The ability to turn a concept into a small package of operational prototypes for use by a unit required a proper yet flexible acquisition strategy that would also set the foundation for increased production later. In turning a concept into an operational prototype, Tobyhanna had to put together a complete drawing package using items from the depot and create the prototype while keeping to strict quality standards.
“We must do everything per Army regulations,” said Joe Lynn, a project manager for Tobyhanna Army Depot, located in Pennsylvania. “So, once everyone came on-site and saw what we do here, and that we’re basically a one-stop shop from concept to combat, it brought a better understanding.”
The process also required constant communication. This came in the form of coordination on the ground during the NTC rotation with the unit’s electronic warfare Soldiers, and during biweekly technical and synchronization meetings involving Tobyhanna, ARCYBER, the Defense Digital Service and RCCTO. Tobyhanna also hosted multiple face-to-face meetings to expeditiously solve technical questions and challenges. On the project management end, RCCTO worked in parallel to address typical program, legal and budget reviews. Of particular note, in addition to constructing the prototype from an engineering concept, the RCCTO, ARCYBER and Tobyhanna put in place a training plan for the 3/1 CD.
SOLDIER INPUT, ON THE GROUND
This rapid approach unfolded on the ground at NTC, as Soldier input went directly to engineers on-site so that they could make changes quickly, sometimes within hours.
“Having that agility really made it possible to have mission success and also to get a lot of feedback to better the system,” Patel said. “Being a newer system and a new tool for a maneuver unit, there are going to be a lot of things we don’t know as [cyber] engineers, and a lot of their specific needs for the capability that may not have gotten through to us. So being out there was very important to this and any other project like it.”
For example, to enhance the overall training experience, RCCTO, Tobyhanna and ARCYBER were able to quickly design and deliver custom mounting systems consisting of cables, brackets and other hardware for vehicle and fixed-site implementation during the prototype deployment at NTC. This fixed-site configuration, part of the unit’s tactical operations center (TOC), was a new design put together days before the unit received it, and proved paramount to Soldiers’ effectiveness in using the system.
“We fielded a completely new configuration kit, the TOC kit,” said Capt. Adam Schinder, commander of the Expeditionary Cyber Support Detachment, 782nd Military Intelligence Battalion. “It was perhaps the most successful implementation of the C-UAS solution. As a result of being statically configured and continuously monitored and plugged in, the unit found the TOC kits extremely successful.”
During the 3/1 CD’s rotation, ARCYBER embedded five Soldiers with the NTC’s opposing force who had the ability to attack the unit with their own “enemy” drones, thus providing more realistic training.
“The system was able to give the supported unit situational awareness of drones that threatened the formation across a wide front,” Schinder said. “It alerted the unit to the presence of the drone, and then it provided automated force protection at the request of the operator. Simply put, we flew the drones, we deployed the devices and we successfully defeated the threat.”
CONCLUSION
This phase-one cyber precision drone detection system will be followed by an upgraded phase-two version slated for delivery to the U.S. Special Operations Command for an operational assessment this summer. Phase two will maximize the capability’s operational life span by incorporating multiple software updates to improve performance. Both efforts will begin to help inform the Army’s overall requirements for cyber-based C-UAS.
Already, RCCTO and ARCYBER are coordinating with partners in the C-UAS community to optimize investments and share technical cyber approaches. They are also advancing new versions that are software-based for easy portability into mounted and dismounted C-UAS platforms.
“Ultimately, the momentum gained through this partnership will increase cyber integration into equipping efforts within the multidomain operations paradigm,” Dillon said. “It’s a great example of the type of partnership that can produce meaningful operational prototypes while setting conditions for transition to programs of record.”
By Nancy Jones-Bonbrest
This article is published in the Summer 2019 issue of Army AL&T magazine.
COL Kevin Finch, Project Manager for Electronic Warfare & Cyber, talks about how his office’s Tactical Electronic Warfare System or TEWS that was part of training and testing during the Joint Warfighting Assessment 2019 on Yakima Training Center, Wash., His team worked with members of the 2nd Brigade, 2nd Stryker Brigade Combat Team, 2nd Infantry Division, to load, test and train the equipment onto their Stryker vehicles.
Additional footage by SGT Gustavo Olgiati, 982nd COMCAM
Rapid acquisition of electronic warfare capabilities served an urgent need, and in the process set an award-winning example of phased prototyping, experimentation and fielding with creative resourcing.
In March 2014, before the rest of the world could react, Russia invaded Crimea, then annexed the region, a peninsula at the southern end of Ukraine. Russia’s subsequent actions in Ukraine revealed electronic warfare (EW) capabilities that not only overwhelmed Ukraine but could rival those of the United States. The U.S. Army Europe (USAREUR) commanding general at the time, Lt. Gen. Ben Hodges, determined that electronic warfare was a critical strategic gap and pushed an operational needs statement to the Pentagon for quick action.
In response, the Army moved electronic warfare to the top of its list for rapid acquisition and endorsed a new approach—phased prototyping, experimentation and fielding—that would incorporate Soldier feedback throughout, infuse new technology as it became available and quickly deliver incremental upgrades to reduce operational risk while informing program-of-record (POR) capabilities currently under development but not yet ready for fielding. This strategy required a creative resourcing approach that combined existing funds, reprogramming actions and a new rapid prototyping program, and ultimately entailed more than 100 separate contract actions.
To formulate and execute the plan, the secretary and chief of staff of the Army tapped the then-newly formed Rapid Capabilities Office (now the Rapid Capabilities and Critical Technologies Office, or RCCTO) and the Project Manager for Electronic Warfare and Cyber (PM EW&C), part of the Program Executive Office for Intelligence, Electronic Warfare and Sensors (PEO IEW&S), to lead the execution of the project, working directly with operational units such as the 2nd Cavalry Regiment in Europe. Less than a year after the project’s approval, the Army fielded new electronic warfare prototypes to select units in Europe, giving Soldiers the ability to implement electronic protection for their own formations, detect and understand enemy activity in the electromagnetic spectrum, and disrupt adversaries through electronic attack effects.

For their efforts in addressing this urgent operational need, the RCCTO and PM EW&C received the 2018 David Packard Excellence in Acquisition Award. The Packard is DOD’s most prestigious acquisition team award. It is given annually to a few select recipients across the armed services and defense agencies for significant contributions demonstrating exemplary innovation and best acquisition practices.
The award-winning effort required teamwork, innovation, a user-centric attitude and a willingness to accept that the prototypes being fielded were just that. They were not completely perfect solutions, but instead incremental advances, with the capability improving at each step as the effort progressed.
Below you’ll read about several of the key players who made the Army’s electronic warfare project a Packard Award-winning reality. However, they are only several of many. Scores of people within the organizations contributed to the success of the project, as did many other individuals and organizations across and outside DOD who were brought in to find new ways to successfully expedite the traditional acquisition process. From EW officers to Army headquarters staff, from cybersecurity experts within the Office of the Assistant Secretary of the Army for Acquisition, Logistics and Technology (ASA(ALT)) to the U.S. Army Test and Evaluation Command, from the Army’s Rapid Equipping Force to industry partners and many others, the achievements leading to the Packard were a team effort that reflects the best of what the Army can do when the stakes are high. Here is a look behind the curtain.
THE DIRECTOR: DOUG WILTSIE
“The big thing for us was speed. Where we had the opportunity to take risks, we did. It started with our board of directors [BOD], which at the time comprised the secretary of the Army, chief of staff of the Army and Army acquisition executive. We briefed the BOD, but there was no requirement to brief anyone else, due to the RCO’s unique charter. So the approval cycle was significantly shorter. The power of the BOD was it allowed us to bring in a broad end-to-end solution for the type of capability we needed to provide. And then, working with the unit, we developed what the specific requirements would be for mounted, dismounted, and planning and management systems. We developed an incremental strategy that increased the capability performance over time. We got prototypes into the hands of the users, who got to train on the equipment and give us continuous feedback on the performance and how to improve it. With this strategy, we fielded the first increment in one year, which was very impressive.”
The power of teamwork: “The user was actually in the lead of this project the entire time. From the delivery of the concept of operations to the performance of the system they wanted, the Soldiers and the EWOs [electronic warfare officers] in those brigades really helped shape how the system was going to operate. They were committed to the incremental strategy, where we put elementary pieces of equipment into their hands first, knowing that the capability was going to get better over time. PM EW&C was the other critical element to this project. The Rapid Capabilities Office had unique authorities but limited people to put on this project, so we partnered with PM EW&C to develop the solutions, prioritize the increments, develop the sustainment process, then together work on a funding strategy for every increment. It was a great partnership.”
Advice for rapid prototyping: “It starts with the user. The rapid approach is really a team sport, and the users are the critical piece on that team.”
THE PROJECT MANAGER THEN: COL. MARTY HAGENSTON (USA, RET.)
“Commanders are severely limited in what they can bring to the electromagnetic spectrum fight. These limitations and lack of options are driving the operational need for EW capabilities.” The operational needs statement (ONS) from U.S. Army Europe “became part of the larger materiel development strategy by design. It provided a mechanism from which to rapidly equip forward presence and rotational forces with initial capabilities, then iterate those based on direct user feedback.
“The ONS provided a superb venue for risk reduction for projected programs, some of which were years away from starting. Not only did the Army benefit from a materiel standpoint, but the effort also drove doctrine, training, organizational design, and tactics, techniques and procedures.” The entire spectrum of doctrine, organization, training, materiel, leadership and education, personnel, facilities and policy benefited, Hagenston said. Likewise, the ONS greatly benefited from programs of record that were underway. These included the Electronic Warfare Planning and Management Tool; Prophet Enhanced; Duke; and Versatile Radio Observation and Direction Modular Adaptive Transmitter, developed by the Intelligence and Information Warfare Directorate of what is now the U.S. Army Combat Capabilities Development Command’s C5ISR (Command, Control, Communications, Computers, Combat Systems, Intelligence, Surveillance and Reconnaissance) Center. “The team was able to leverage these programs, which helped our velocity by providing a critical foundation for the ONS.”
The key to success: “The real force behind the success of this effort was the teamwork, leadership support, stable resources and direct access to the customer. The approach itself was simple. First, we took what we had and adapted it to the operational problem. This served as Phase 1, or the minimum viable product. Once we deployed Phase 1, 12 months from receiving resources, we were able to take the direct user feedback and prototype something closer to what the units wanted. This served as Phase 2. Through all of the phases, the capabilities evolved based on direct user feedback. Our team carefully listened to the feedback and worked in those changes. In many cases it was done on the spot, while other changes were saved to the next logical insertion point.”
Advice for rapid prototyping: “First, get intimate with the operational problem. Second, get the minimum viable product out quickly and really listen to the direct user feedback. Finally, iterate as fast as possible based on the direct user feedback. Velocity is the real advantage.”
THE PROJECT MANAGER NOW: COL. KEVIN FINCH
“Rapid prototyping will have a very positive effect on the long-term POR. It also shows us the current state of industry. Specifically, in the EW specialty, rapid prototyping coupled with quick reaction capabilities [QRCs] has effectively informed the community on possible innovative solutions that help the U.S. pace the threat. The QRCs we are currently fielding to the force have enabled the program office to determine if innovative solutions are viable for long-term PORs. In FY20, PM EW&C will use the lessons learned from the QRC and rapid prototypes to inform the development of the long-term Terrestrial Layer System.”
What are the next steps for the effort? “The ONS for Europe maintains the ongoing effort until the POR comes on board. We have already provided an initial capability and are on schedule to provide a Phase 2 capability in FY19. This new capability will provide a significant improvement over Phase 1 while informing both the development of the POR and the Army’s decision-making on fielding quantities and timelines.
Also, with “The U.S. Army in Multi-Domain Operations, 2028” concept published, capabilities in the electromagnetic spectrum [EMS], cyber and space will become better integrated into operations. Niche systems will no longer operate in stovepipes, but will become integrated and synchronized with operations occurring in all the domains: land, air, sea, cyber and space. Systems such as the [Electronic Warfare Planning and Management Tool], which links and synchronizes the EMS to the tactical commander, will become increasingly important.”
Advice for rapid prototyping: “Implementing a rapid approach has to be a collaborative team process built on the adaptation of lessons learned and best practices. As PM EW&C moves into the second iteration of our rapid processes, hard timelines closely linked to the operational force’s needs will drive timely and responsive decision-making. Ultimately, the success of a rapid approach is highly dependent on buy-in from all the team members, including industry partners and external stakeholders.”
THE PRODUCT MANAGER: LT. COL. ERIC BOWEN
“This is the outcome of a Soldier-inclusive, Soldier-driven endeavor. Their feedback laid the blueprint that guided our multiphased approach, serving as our engine of innovation. We had continuous engagements with Soldiers who received the equipment, including from Stryker, armor and airborne infantry brigades. Although the initial phase repurposed existing equipment, the feedback identified additional enhancements needed, such as how information was presented to the operator, how it was reported to higher headquarters and how it should be installed in the vehicles for optimal use. This feedback also identified a need for additional vehicle platforms that would support light, expeditionary operations, as well as for sensors that Soldiers could easily carry and operate during dismounted operations. These capabilities, which we didn’t address initially, were prioritized for the follow-on delivery phases.”
The toughest challenge? “The ‘horizontal’ or system-of-systems integration and end-to-end engineering, because various sensors needed to function as a networked set. To make it all work, we needed to stitch together existing sensors that existed as both PORs and QRCs, in order to provide a common operating picture to our EW planning and management tool.”
Advice for rapid prototyping: “Keep priority on delivering the product on time. You are subject to the tyranny of time, and the solution delivered will not be perfect. It never will be. There are no more ‘drive-by fieldings,’ so forge a solid commitment with the user, who will shape development before delivery—and cultivate that relationship to fix, improve and maintain the equipment to ensure mission success. You are delivering more than just materiel; these capabilities will influence doctrine, change organizations and challenge policy to enable commanders and higher Army echelons to respond to rapidly evolving worldwide threats.”
THE MONEY: SONJA HOLZINGER (PM EW&C)
“This rapid prototyping approach dictated an agile, adaptive business model. That meant the two business teams had to come together and determine how much the effort would cost, what type of funding was needed, what contract vehicles should be used and what resources were available.”
“Early on, as the acquisition strategy and technical requirements were being refined, we implemented a tailored work breakdown structure into all cost estimating efforts. This enabled the teams to accurately account for all costs associated with rapid prototyping and develop a cost estimate, which was later used as the basis for the spend plans. Throughout the whole process, strong collaboration and daily communication was the key. PM EW&C Business Management Division was heavily engaged in identifying what funds were needed and where they should be sent. The RCCTO Business Management Division was responsible for ensuring funds were provided on time and in the amount needed. The two teams worked as one toward accomplishing the same goal. The USAREUR ONS was executed almost 100 percent within the cost estimate, on time and without any unfunded requirements.”
What contracting mechanisms were used? “The business teams worked together to develop a funding strategy to ensure the effort was fully funded. Initially we reallocated existing funds for this effort. We also utilized mechanisms such as below-threshold and above-threshold reprogramming actions. We successfully applied for and received funding from the Office of the Secretary of Defense Rapid Prototyping Program. To meet a very tight timeline for delivery, we also worked closely with [the U.S.] Army Contracting Command, as well as the Navy and Air Force contracting commands, for select contracting actions.
“We coordinated execution of more than 100 contract actions, including contract modifications, task orders and delivery orders. In some instances, because of the urgency of the requirement and the government’s interest to start contract work early, we used un-definitized contract actions.”
Advice for rapid prototyping: “This is a great approach to quickly provide needed capabilities to our warfighters. Constant collaboration and communication with the project manager, contracting team, business team and all stakeholders involved in your program is a must. This allows you to identify and address any risks or issues early.”
THE ENGINEER: BRANDON LITTLE-DARKU
“As the project lead and lead systems engineer on EW for the RCCTO, I worked in close partnership with the PM EW&C team and my counterpart there, Lt. Col. Bowen, to develop and deliver this capability. Having a strategic focus and directing this capability not to the entire Army, but to brigade-and-below operations within the European theater, proved a key to our success. Focusing on the units aligned to USAREUR and understanding their concept of operations helped to scope not only the capabilities required of the various systems, but also how they needed to be integrated into the formations and the tactical mission command network. That, paired with early and continuous engagement with the brigade combat teams aligned to USAREUR, helped scope the effort and shape the overall phased approach for addressing the operational requirements.”
The toughest challenge? “Making sure we met all the requirements possible, which included establishing a networked EW capability that could interoperate with Army mission command systems, while also meeting our delivery timeline. The team included a great set of dedicated professionals within the RCCTO and the PM, and across our partners throughout the Army, that made this unprecedented effort a success.”
Advice for rapid prototyping: “Perfection is the enemy of ‘good enough’ when building your acquisition strategy and scoping out the phases of the capability. Time will always be one of the critical measures of success, and the burdens associated with the endless pursuit of perfection will always be a hindrance to getting the required capabilities to the end user. Working directly with the users early in the process, and then continuing to receive their input and operational feedback throughout the process, proved key to making sure we developed and delivered what they needed to meet their mission.”
THE USER: CAPT. SEAN LYNCH, (2ND CAVALRY REGIMENT)
“This equipment provides additional sensors that units can leverage to help build a common operating picture and drive the targeting process. It provides commanders with additional options to more effectively shape their areas of responsibility, while also addressing theaterwide challenges from near-peer competitors and NATO adversaries. These assets can be seamlessly integrated within a Stryker formation, require no reliance on joint air platforms, and can provide immediate direction finding or geolocating capability of enemy emitters to maneuver commanders at the lowest levels. The Army can continue to build on this momentum by solidifying what the primary mission or role of ground-based electronic warfare is and how the Army feels it should be equipped to accomplish it.”
How did partnering with the acquisition team early work for your unit? “Exceedingly well. Our team was fortunate to be able to participate in multiple Network Integration Evaluations, simulation exercises, and testing events both pre- and post-fielding. This gave our regimental planning team and tactical operators several instances to provide direct, candid feedback to the engineers, acquisition team and decision-makers involved in the project. We were able to see our ideas and feedback incorporated almost immediately, and knew with high confidence what we were receiving as the end user. This also served to get Soldier buy-in at the lowest levels, and they became more vested in providing comprehensive and meaningful feedback. It also removed a lot of unnecessary guesswork and ensured all parties had a shared understanding and shared expectations of the scope of the fielding.”
Advice for rapid prototyping: “Partner early and consistently with the acquisition team before, during and after equipment fielding. Know those aspects of the equipment that are more important to you and your Soldiers, and be prepared to communicate those requirements clearly. It’s also important to build a plan on how to go about stressing new systems, capturing relevant information, and how you envision the systems or equipment will be employed.”


For more information on the Army RCCTO, go to rapidcapabilitiesoffice.army.mil. For more information on PEO IEW&S and PM EW&C, go to peoiews.army.mil.
Story by Nancy Jones-Bonbrest, John Higgins and Claire Heininger – U.S. Army Acquisition Support Center
Photo by US Army SGT Amber I. Smith
NANCY JONES-BONBREST is a public communications specialist for RCCTO. She has written extensively about Army modernization and acquisition for several years, including multiple training and testing events. She holds a B.S. in journalism from the University of Maryland, College Park.
JOHN HIGGINS is a public affairs writer for PEO IEW&S. He is an Iraq War veteran and former public affairs Soldier. He holds a B.A. in film production from Towson University.
CLAIRE HEININGER is the public communications lead for RCCTO and has written extensively about Army acquisition topics. She holds a B.A. in American Studies from the University of Notre Dame and is a former politics and government reporter for The Star-Ledger, New Jersey’s largest newspaper. She is Level II certified in program management.
This article was originally published in the Spring issue of Army AL&T magazine.
JOINT BASE LANGLEY-EUSTIS, Va. (AFNS)– —
Air Combat Command is merging 24th and 24th numbered Air Forces at Joint Base San Antonio-Lackland, Texas, this summer to better integrate cyber effects, intelligence, surveillance and reconnaissance operations, electronic warfare operations and information operations.

The synergy between cyber, ISR, EW and IO will increase unity of effort across these capabilities, resulting in new and improved options for combatant commanders. The integration also better aligns these units with priorities outlined in the 2018 National Defense Strategy and delivers the first “Information Warfare” NAF for the Air Force.
“The merger of 24th and 25th is the next step in leveraging and integrating new ideas and technologies to both improve the quality and speed of decision-making and deliver improved effects for commanders,” said Gen. Mike Holmes, ACC commander. “This formalizes the existing collaborations between cyber and ISR while expanding our competitive space in EW and IO, ultimately improving readiness and increasing lethality across the range of military operations – all vital to the success of multi-domain warfighting in the 21st century.”
The new IW NAF bolsters the Air Force’s ability to present electromagnetic spectrum forces and capabilities to execute missions alongside joint and interagency partners.
While the final organizational structure has not yet been determined, ACC anticipates an activation ceremony at JB San Antonio-Lackland, Texas, in late summer of 2019.
Story by Air Combat Command Public Affairs. Graphic by Mr Robert Young.
GUHOR Stick? What the heck is a GUHOR Stick and what does it have to do with SSD? Well, as some of you may know, I spent the first half of my career in the Army MI business, primarily as a SIGINTer. Since the Army in its infinite wisdom decided to dismantle and then stovepipe its IW capability over the past 25 years, I feel it’s important to revisit the history of the SIGINT business as it is recreated in the form of Cyber Electro Magnetic Activities, or CEMA.
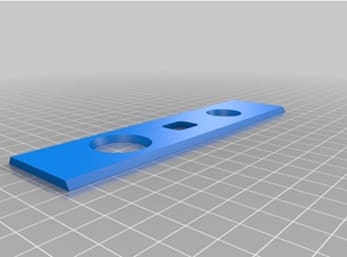
The GUHOR Stick is one of the most important tool ever invented for the traffic analyst (TA). Solutions to the most intricate communications networks often began with this simple device.
No self-respecting TA was ever without one close at hand. Like the six-shooter of the old West, the analyst kept it at his or her side, always ready to draw- circles, boxes, and lines.
The GUHOR Stick, in its most recent and best known iteration, is merely a 6? by 1.5? clear plastic template. Its prime purpose is to facilitate the drawing of communications diagrams, although its secondary uses are endless. It comes equipped with a large circle at one end to draw control terminals, a smaller circle at the other end for outstations, and a small rectangle in the center for communications relays and collective (CQ) calls. The straight edges are used to connect these stations and show communications paths. With this tool, a #2 pencil (with extra erasers), some graph paper, and several pencils of various colored leads, the analyst of old was fully prepared to face any communications adversary.
GUHOR Stick! But where did this strange name come from? Putting my analytical skills to work, I set out to research the issue. To my surprise, there was a higher than expected number of individuals who had heard the name. Most were seasoned veterans from a mixture of professions, including linguists, reporters, managers, executives, and, naturally, traffic analysts. But there was more than a little discussion about what this device was and where its name originated.
The early returns were mixed, however. I was still searching for the definitive word. It was at this point when I began to get responses from members of a Communications Analysis Association (CAA) interest group. A number of seasoned veterans recounted their GUHOR experiences and, in a number of colorful responses, gave me what I believe to be the true scoop.
GUHOR Sticks as traffic analysis tools have been around for decades. Some CAA respondents remembered seeing or using them in one form or another from at least the early 1960s. Even so, a couple of questions remain unanswered. Who invented it? Why was it given this curious name? Someone out there knows. If you can solve the mystery, we (Station HYPO) are ready to hear a good story.
All this discussion about GUHOR Sticks may be moot. These devices are few and far between these days. The GUHOR Stick does not have a federal stock number. They were made in batches at NSA by special order; however, they are fast becoming collector items. With the advent software, many analysts are using computer graphics to diagram their targets. The traditional circles and lines on paper are becoming passé. Most GUHOR Sticks that are found are being employed for many a sundry task-not for crafting the intricate networks of old, but for drawing nondescript lines and symbols unrelated to the trade of traffic analysis.
Those on field duty in the Pacific used a similar device which they called a “pooka-maker.” Pooka is a Hawaiian word for “hole.”
Source: NSA CRYTPOLOG July, 1994 (MDR Case #54778)
Edited by Mario Vulcano
To read more history, visit Station HYPO.

FORT IRWIN, Calif. — The Army’s newest electronic warfare vehicle was tested at the Army’s toughest training ground, the National Training Center in Fort Irwin California in January.
Electronic Warfare Soldiers from 3rd Armored Brigade Combat Team “Greywolf,” 1st Cavalry Division conducted electronic attack and electronic support operations during the month-long exercise using the Electronic Warfare Tactical Vehicle (EWTV).
“Our main purpose was to provide support by denying communications to the enemy, jamming comms,” said Sgt. First Class Cristian Holguin, the EWTV team leader. “In addition we were able to listen in on FM communications from the enemy and detect enemy electronic signatures to use for call for fire missions.”
The brigade received the Army’s first dedicated electronic warfare vehicle in September of 2018 in time to test it out during the Brigade’s external evaluation, Pegasus Forge III, at Fort Hood, Texas. The team then provided feedback to the team at the Rapid Equipping Force, which had developed the vehicle.

“It’s like version one of the system. And for being version one it is a very good system,” said Holguin. “The folks at REF listened to our feedback following Pegasus Forge and actually were making upgrades to the vehicle as we were on ground at NTC.”
According to Staff Sgt. Darron McCracken, a EWTV operator, the shortened timetable between Pegasus Forge and NTC presented a challenge to the team, but they were able to overcome them and help integrate the system fully at the brigade and battalion-levels.
“Initially the battalions were a little skeptical of the system. Not only was it an asset they had to provide forces to help protect, but it’s a pretty big vehicle as well,” he said. “But once they saw what it could do and they benefited from its effects, they recognized the benefits of the system.”
The near-peer enemy along with the terrain and elements that the Brigade faced at NTC made it an ideal environment to test the EWTV. Once the force-on-force fight was completed, the team conducted situational training that helped further test the capabilities of the vehicle.

“We worked on finding ways to better improve our jamming and detection capabilities,” said Staff Sgt. Francisco Becerra, a EWTV Operator. “For instance, we learned by raising the antenna two more inches we were able to getter better lines of bearing. These are things that you can’t necessarily test out in the middle of a fight.”
Measuring the performance of the vehicle at NTC was sometimes difficult to do since there was no immediate feedback through real time measures and sensors. According to Holguin it is something that NTC is working to improve, however they were able to validate and measure effects in other ways.
“There are two aspects of performance. Performance of the equipment and performance of the teams themselves,” Holguin said. “And I think we’ve accomplished more than we expected for integration and employment; having and using the EWTV validated our position as an effective asset on the battlefield.”
Greywolf was the first to test the vehicle in an austere environment against a near-peer foe, but they won’t be the last. The EWTVs belong to III Corps and are being moved to other units so that their teams can test them and add their inputs to improve the system.
“The intent is to take all of the lessons learned and build on it,” said McCracken. “Towards the end of the process we will have an SOP, something that is predictable and can be translated across the Army.”
When asked if, after testing it out at NTC, they felt it was an effective system, McCracken answered, “Absolutely. Absolutely.”
The new vehicle was developed to provide Army Electronic Warfare Teams with the ability to detect and attack in the electromagnetic spectrum from an operationally relevant range at the brigade combat team level. It was developed by the Rapid Equipping Force to give the Army’s Brigade Combat Team a dedicated electronic warfare vehicle.
By CPT Scott Kuhn
FORT IRWIN, Calif. — Army cyber warriors often say one of the things they like about cyber as a career is that it offers the challenges and opportunities of engaging in cyberspace operations either at a desk or in a tactical environment.

Sgt. Alexander Lecea, Spc. Ashley Lethrud-Adams and Pfc. Kleeman Avery are Cyberspace Operations Specialists assigned to the Expeditionary Cyber Support Detachment (ECSD), 782nd Military Intelligence Battalion (Cyber) who were recently at the National Training Center, supporting a training rotation for a battalion from the 3rd Brigade Combat Team (BCT) of the 1st Cavalry Division.
All three say they chose an Army cyber career because of that mix — being able to move between working in an office and taking part in operations and exercises.
The detachment provides, “A little bit of both aspects of the cyber field,” Lecea said. “You get hands-on technical training — you can do this job in an office. But at the same time you can do it in the field. And there are real-world applications.”
While cyberspace operations can be done in an office, it’s not as effective as being on the ground with maneuver units, the sergeant said.
During training exercises such as this rotation in the southern California desert, the trio functioned alongside the cavalry battalion as an Expeditionary Cyber Team that provided cyber effects and intelligence for the rotational training brigade, Lecea said.

“We provide the maneuver commander with cyber effects and support the troops on the ground,” working in concert with the 3rd BCT’s Electronic Warfare officer and Cyber Electromagnetic Activities (CEMA) chief, Lecea explained, to achieve the brigade commander’s intent and guidance.
Lecea said he went became a cyber warrior because he, “wanted to do something that was challenging and rewarding and also have applications outside the Army. It’s one of the toughest [Military Occupational Specialties], but at the same time I feel that it’s the most rewarding. You have a lot of challenging situations and you have to use your brain. You have to have good teamwork, too.”
The sergeant said he isn’t sure if he will stay in uniform long-term, but added that the Army also offers training opportunities that will prepare him for the future, whether or not he reenlists.

“We’re talking about SEC+, NET+, a lot of industry standards certifications you’ll need outside in the civilian world to get hired. It’s all the stuff they look for,” he said.
“I was interested in the field and I didn’t just want to go to college, so I joined Army Cyber,” said Lethrud-Adams. “The Army is a great opportunity because you’re getting paid to learn all this stuff and you get experiences you wouldn’t get elsewhere in the world. You’re not going to get experiences like this in college.”
Lethrud-Adams said his favorite part of cyber operations is malware analysis, and his two teammates vehemently agreed.

Avery, the newest Soldier on the team, said he wants to become an ION (Interactive On-Net Operator) and eventually join the FBI.
Until then, he said, he enjoys the challenges of cyber operations and trying to figure things out.
Story and photos by Steven P. Stover, INSCOM.