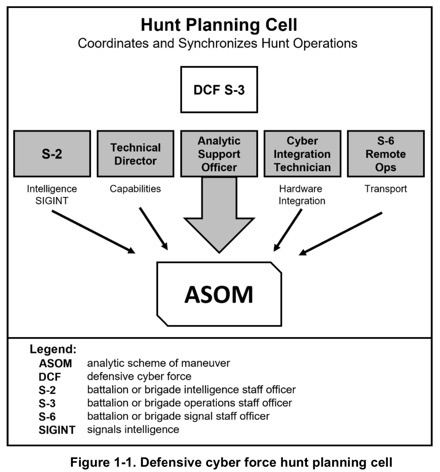
PETERSON SPACE FORCE BASE, Colo. — The U.S. Army’s top generals for cyber, space and special operations forces met to discuss the Triad partnership and how they can further develop, operationalize and institutionalize the collaboration.
Commanding Generals Lt. Gen. Maria B. Barrett, U.S. Army Cyber Command; Lt. Gen. Jonathon P. Braga, U.S. Army Special Operations Command; and Lt. Gen. Sean A. Gainey, U.S. Army Space and Missile Defense Command, met Jan. 31, 2024, for the third Triad 3-Star General Officer Steering Committee at USASMDC headquarters at Peterson Space Force Base.
Members of the committee emphasized the importance of the Triad due to the ever-changing character of warfare. Along with this evolution, the threats and the nature of deterrence are changing for the United States. The Triad looks to develop innovative and comprehensive solutions.
“The Cyber-Space-SOF Triad provides one of these solutions,” Braga said. “It is a ‘Modern-Day Triad’ designed to converge unique accesses, capabilities, authorities, understanding and effects in many of the same ways we have implemented combined arms operations. Additionally, the Triad provides operational and strategic advantage during active campaigning, crisis and conflict, while presenting options to senior leaders that are less escalatory than current strategic deterrence options.”

Gainey said that they must continue building upon the significant progress the Triad has already made in the development of concepts, capabilities and formations that enable exquisite operational preparation of the environment. The commands have already developed a unified exercise, experimentation and engagement plan for fiscal year 2024 and fiscal year 2025.
“We are working with the Theater Special Operations Command to ensure they know the space and high-altitude capabilities we can provide and to develop the operational concepts of employment,” said Gainey.
“(The Triad) is developing real-world employment concepts designed to enable Army and joint force objectives anywhere in the world at a time and place of our choosing,” Gainey said. “Additionally, the Triad will enable ‘Left of Launch’ trans-regional missile defeat and active campaigning to ensure the ability of our nation’s adversaries to strike the United States, as well as its partners and allies is prevented.”
The Triad is a major way we can contribute to multi-domain operations and for us, the potential it provides our Missile Defeat efforts, as well as the access, understanding, and effects it can enable for the Joint Force are undeniable, Gainey said.
“As such, the Triad provides flexible deterrent options that can shape the threat environment in ways our adversaries are unaware of and can provide flexible response options if they choose to break international norms and escalate tensions into conflict,” he said.
Braga said the Triad has an outsized impact against the adversary’s capabilities as it relates to SOF, space and cyber.
“That is why it is inherent we work together, experiment together and learn together,” Braga said.
Barrett said the Triad is coming up with solutions and tools together as a team.
“Triad operations disrupt adversary actions, demonstrate resolve, shape the adversary’s perceptions and gain advantage for warfighters when deterrence fails,” Barrett said. “ARCYBER has a track record of integrating cyber, electronic warfare and influence operations and can now deliver that to triad partners.”
By Dottie White, USASMDC