WASHINGTON — The Army plans to use one of the largest exercises in Europe since the Cold War to pilot new tactical space technology that will help Soldiers carry out mission command on a multi-domain battlefield.

An initial prototype of TITAN — Tactical Intelligence Targeting Access Node — will be tested during the Defender-Europe 20 exercise next spring. The exercise is set to have about 37,000 U.S. and European troops training in 10 nations across the continent.
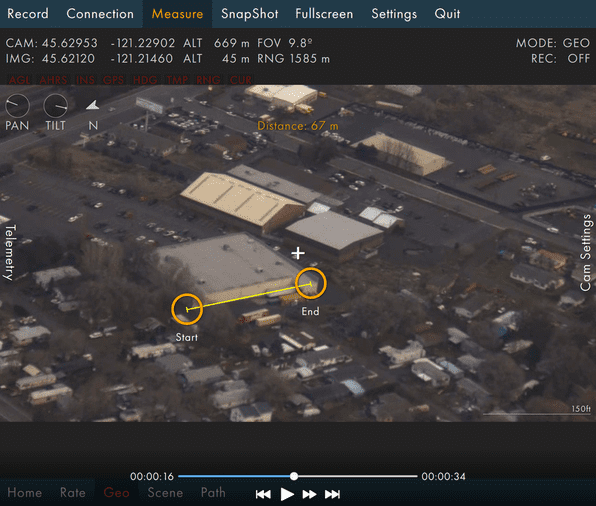
The TITAN system, which is a scalable and expeditionary intelligence ground station, leverages space and high altitude, aerial, and terrestrial layer sensors to provide targetable data to fires networks. It also provides multi-discipline intelligence support to targeting, and situational awareness and understanding for mission command.
Today, the Army has roughly 100 tactical ground stations, 13 operational ground stations and a few other dissemination vehicles to inform battlefield commanders, said Brig. Gen. Rob Collins, Program Executive Officer for Intelligence, Electronic Warfare and Sensors, or PEO IEW&S.

But “some of those are more specific to the echelon,” he said Oct. 16 at the Association of the U.S. Army Annual Meeting and Exposition. “They’re not necessarily tailorable, easy to use or expeditionary as we want them to be.”
TITAN aims to consolidate much of those capabilities to better provide “deep sensing” information from intelligence, surveillance and reconnaissance sensors from all domains.
It also ties deep sensing to long-range precision strike options to defeat enemy anti-access/aerial denial environments, officials said.
An industry day is scheduled for Dec. 4 at Aberdeen Proving Ground, Maryland, to further discuss the way forward with TITAN.

A TITAN space prototype is expected to be delivered by early fiscal year 2022.
“How do you bring those ground stations together in one platform, or a series of platforms, that are modular, scalable and [with] open systems architecture,” said Willie Nelson, director of Army Futures Command’s Assured Positioning, Navigation and Timing Cross-Functional Team.
Collins said they are looking for a modular “Lego approach” for the system that will go through an iterative testing process, starting with the Defender exercise.
It is then expected to be rolled out in another exercise in the Pacific region to get additional user feedback later next year, Nelson said.
TITAN will fit into the Army’s Multi-Domain Task Forces being built up in the Pacific and in Europe. The system will work with the task force’s unit called I2CEWS, which stands for intelligence, information, cyber, electronic warfare and space.
It will “absolutely be part of that task force to be able to see deep and target deep,” Collins said. “It’s going to be a key capability, key enabler.”
TITAN will also play a large role in the Army’s space strategy, in which one of its main areas is battle management command and control.
“It’s leveraging both commercial and military capabilities to be able to provide eyes and ears on the battlefield for our Soldiers and our platforms,” Nelson said.
Since the sensors will compile massive amounts of data, TITAN will need to rely on artificial intelligence and machine learning to sift through it.
“As we start pulling in all this data, there’s going to be a significant and overwhelming amount for our intelligence Soldiers to be able to process,” Collins said.
The goal will then be to quickly deliver easily-digestible data to Soldiers in combat and to their systems.
“We just don’t collect this data for the sake of collecting it,” Collins said. “We collect it so that we can distribute that to kinetic, non-kinetic weapon systems and for commanders to be able to make decisions on the battlefield.”
By Sean Kimmons, Army News Service